EOL IT Services has now merged with tier1 Asset Management Ltd
IT Lifecycle Services – with impact at our core.
tier1 is the UK’s number one circular economy lifecycle services business
“tier1 is the UK’s number one circular economy lifecycle services business”

Why are we unique? Security. Sustainability. Social Value.
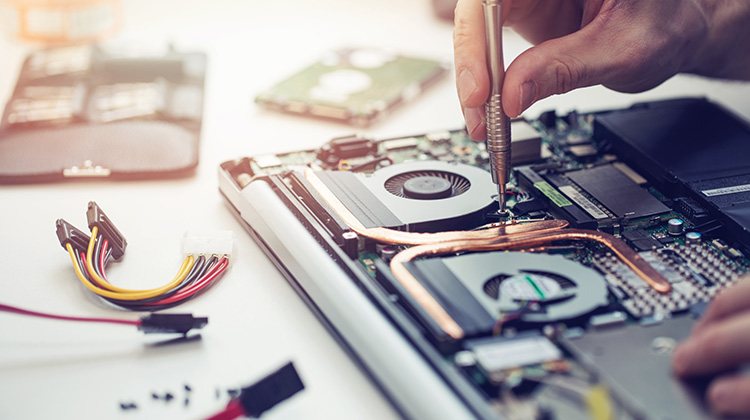
tier1’s suite of IT Asset Lifecycle services ensures that our clients mitigate the risks associated with securely managing IT assets throughout their lifecycle.
But we are so much more than that! Our unique social value proposition, the highest level of data security, circular and sustainable approach and full suite of multi-channel routes to market for resale, make us the only lifecycle services business to work with today.
How can we help?
An outstanding service provider within this sector we provide an extensive and security focused range of IT Lifecycle services in support of our clients.
WORK WITH THE BEST
There’s a reason we’re the UK’s number one.
We continually strive to provide our clients with tier1’s ongoing commitment of trust, security, quality and confidentiality. Our strategy has always been to achieve every possible certification standard to prove the quality and security of the service we provide.






































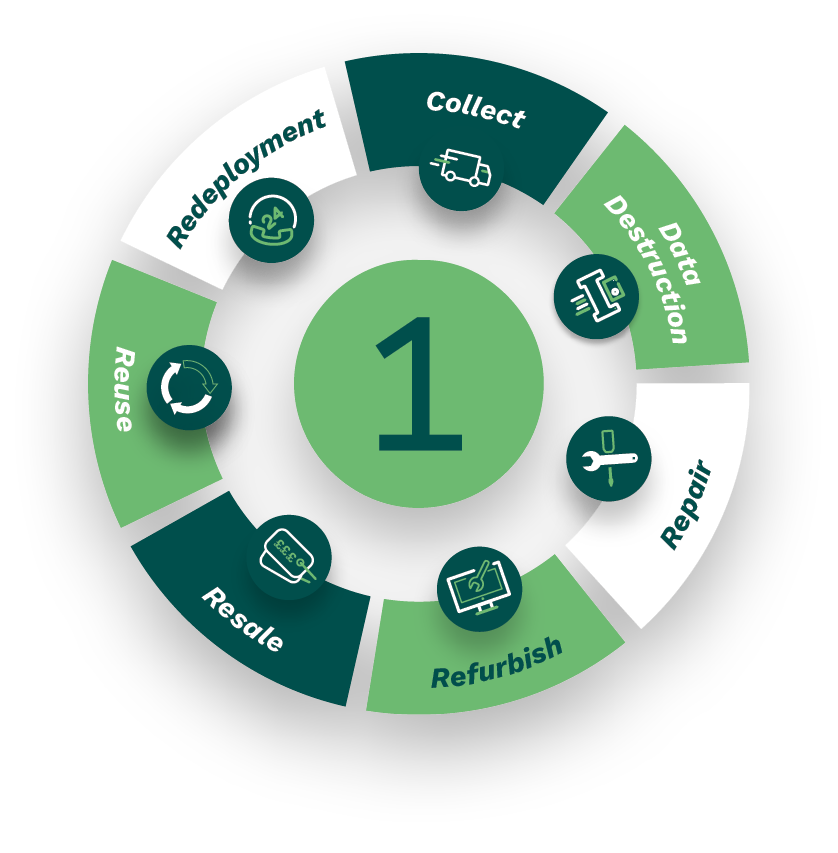
Reduce. Reuse. Refurbish. Redeploy.
Circular Approach to Sustainability.
We ensure that the Lifecycle Services we provide are sustainable and circular in approach, and actively promote the reuse of all equipment where possible. We work closely with our clients to improve awareness of environmentally favourable solutions, ensuring recycling is the last option considered and making a real contribution to your ESG goals.
Reduce. Reuse. Refurbish. Redeploy.
Circular Approach to Sustainability.

We ensure that the Lifecycle Services we provide are sustainable and circular in approach, and actively promote the reuse of all equipment where possible. We work closely with our clients to improve awareness of environmentally favourable solutions, ensuring recycling is the last option considered and making a real contribution to your ESG goals.
Premium Refurbishment
We believe in second chances.
High quality enterprise equipment can be refurbished to extend its usable life. When customers buy a device refurbished by tier1 they avoid new carbon emissions. For example, a refurbished laptop saves approximately 200kg CO2e compared to buying new, which is a 75% reduction in carbon footprint per device.
Premium Refurbishment
We believe in second chances.
High quality enterprise equipment can be refurbished to extend its usable life. By refurbishing and reusing IT equipment we are reducing and avoiding new carbon emissions. Carbon savings of a refurbished device versus new are 225kg CO2e per device which is a 75% reduction in carbon footprint per device.
News & Views
The Hidden Environmental Impact of Our Smartphones.
Checking emails, social media or the news; banking, making payments, taking photographs, finding...
Delivering Social Value Through Our Business Operations
We have become increasingly aware of economic, social and environmental issues. Our renewed sense...
Navigating the Subjectivity of Refurbished IT Devices
Reconditioned, renewed, pre-owned… as there are no hard and fast definitions of what the phrase...
The Hidden Environmental Impact of Our Smartphones.
Checking emails, social media or the news; banking, making payments, taking photographs, finding...
Delivering Social Value Through Our Business Operations
We have become increasingly aware of economic, social and environmental issues. Our renewed sense...