EOL IT Services has now merged with tier1 Asset Management Ltd
News & Views.

The Hidden Environmental Impact of Our Smartphones.
Checking emails, social media or the news; banking, making payments, taking photographs, finding our way; it is fair to say that we would be lost without our smartphones, perhaps literally. Oh, let’s not forget, our now indispensable devices also make calls. Essential...

Delivering Social Value Through Our Business Operations
We have become increasingly aware of economic, social and environmental issues. Our renewed sense of community, which naturally came into focus during Government lockdowns, furthered the opportunity for ethical businesses to drive social impact, rather than simply be...

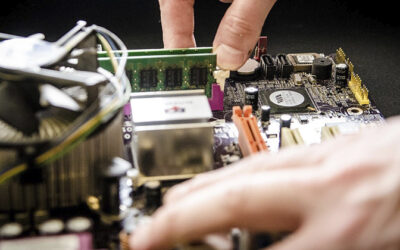
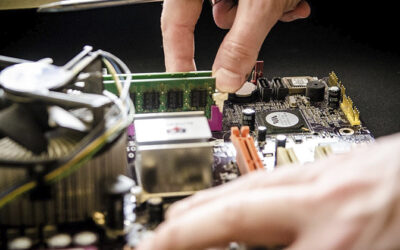
Navigating the Subjectivity of Refurbished IT Devices
Reconditioned, renewed, pre-owned… as there are no hard and fast definitions of what the phrase ‘refurbished technology’ means, purchasing restored devices can feel a little like navigating a minefield. This confusion, poor experiences or deep-rooted misconceptions...

Can Data Centres Ever Be Green?
With colossal energy consumption and emissions generated, the world’s data centres have faced heavy criticism for some time due to their environmental impact. Many still rely on non-renewable forms of power, waste staggering quantities of water annually within the...

How to Safeguard Your IoT Infrastructure & Your Business
Delivering real-time data-driven insights and transformative business process automation at the touch of a button, the Internet of Things (IoT) is a substantial economic driver for global organisations. By optimising operations to improve productivity and performance,...
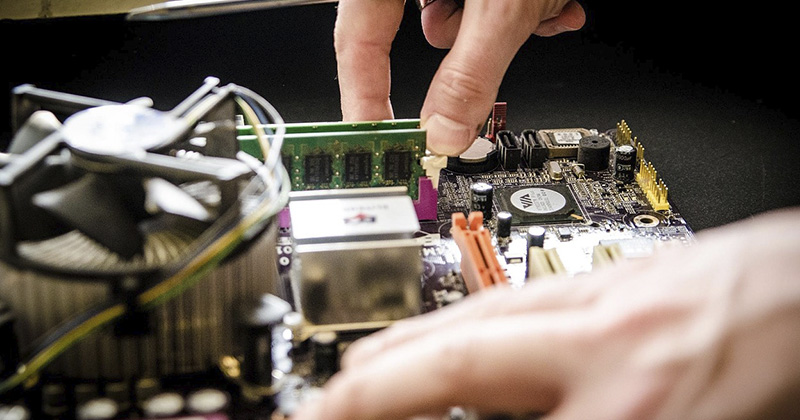
Navigating the Subjectivity of Refurbished IT Devices.
Reconditioned, renewed, pre-owned… as there are no hard and fast definitions of what the phrase ‘refurbished technology’ means, purchasing restored devices can feel a little like navigating a minefield. This confusion, poor experiences or deep-rooted misconceptions...

Is AI Bad for the Environment?
Ask ChatGPT if AI is bad for the environment and you’ll get the following response. “The environmental impact of artificial intelligence is a complex and multifaceted issue”. Driving digital transformation, AI is certainly moving up board meeting agendas at speed,...

5 Benefits of the IT Reverse Supply Chain.
Ethical supply chain practices have increased in priority in recent years as many more organisations align with the UN Sustainable Development goals. In particular, goal 12, Responsible Production and Consumption. Sustainability compliance is also top of the agenda...

Turbocharge your 2024 IT Budget – Turn Your Bottom Line Green.
The majority of organisations are facing tough financial choices; budgets are under close scrutiny with leaders making sure that money is spent wisely. With business technology amounting to a significant portion of overall expenditure, optimising your IT budget is...

The CSRD: Sustainability Reporting Steps up a Gear.
The European Union’s WEEE directive showed the rest of the world how e-waste legislation should be done, and driven by the member states’ commitment to climate neutrality, the new Corporate Sustainability Reporting Directive (CSRD) is set to do the same when it comes...
Recent Stories
Categories
Get in touch and see
how we can help.
Either fill in the form below or give us a call to speak to one of our friendly team.
The Hidden Environmental Impact of Our Smartphones.
Checking emails, social media or the news; banking, making payments, taking photographs, finding our way; it is fair to say that we would be lost without our smartphones, perhaps literally. Oh, let’s not forget, our now indispensable devices also make calls. Essential...
Delivering Social Value Through Our Business Operations
We have become increasingly aware of economic, social and environmental issues. Our renewed sense of community, which naturally came into focus during Government lockdowns, furthered the opportunity for ethical businesses to drive social impact, rather than simply be...
Navigating the Subjectivity of Refurbished IT Devices
Reconditioned, renewed, pre-owned… as there are no hard and fast definitions of what the phrase ‘refurbished technology’ means, purchasing restored devices can feel a little like navigating a minefield. This confusion, poor experiences or deep-rooted misconceptions...
Can Data Centres Ever Be Green?
With colossal energy consumption and emissions generated, the world’s data centres have faced heavy criticism for some time due to their environmental impact. Many still rely on non-renewable forms of power, waste staggering quantities of water annually within the...
How to Safeguard Your IoT Infrastructure & Your Business
Delivering real-time data-driven insights and transformative business process automation at the touch of a button, the Internet of Things (IoT) is a substantial economic driver for global organisations. By optimising operations to improve productivity and performance,...
Navigating the Subjectivity of Refurbished IT Devices.
Reconditioned, renewed, pre-owned… as there are no hard and fast definitions of what the phrase ‘refurbished technology’ means, purchasing restored devices can feel a little like navigating a minefield. This confusion, poor experiences or deep-rooted misconceptions...
Recent Stories
Categories
Get in touch and see
how we can help.
Either fill in the form below or give us a call to speak to one of our friendly team.
The Hidden Environmental Impact of Our Smartphones.
Checking emails, social media or the news; banking, making payments,...
Delivering Social Value Through Our Business Operations
We have become increasingly aware of economic, social and...
Navigating the Subjectivity of Refurbished IT Devices
Reconditioned, renewed, pre-owned… as there are no hard and fast...
Can Data Centres Ever Be Green?
With colossal energy consumption and emissions generated, the...
How to Safeguard Your IoT Infrastructure & Your Business
Delivering real-time data-driven insights and transformative...
Navigating the Subjectivity of Refurbished IT Devices.
Reconditioned, renewed, pre-owned… as there are no hard and fast...
Recent Stories
Categories
Get in touch and see
how we can help.
Either fill in the form below or give us a call to speak to one of our friendly team.